UK Government figures released earlier this year show around a third of UK businesses suffered an IT security breach or attack in the past 12 months.
There is an easy way for your organisation to ramp up your security in response to this increasing threat: implement two-factor authentication.
The Netstar team explains two-factor authentication through a Q&A format; answering common questions about what two-factor authentication is and how it can help.
Where do these cyber security statistics come from?
The UK Government’s own statistics show around a third (32%) of businesses and two in ten charities (22%) reported having cyber security breaches or attacks in the last 12 months. This figure rises to 60% among medium businesses which identified a breach or attack. For the average large business, the financial cost of attacks over the past 12 months was £22,760 – with some attacks costing significantly more.
What can businesses do to protect themselves?
Access control and encryption have traditionally been the two stalwarts of organisational approaches to cyber security.
Access has traditionally been managed and authenticated through the use of usernames and passwords, but there is significant evidence this is no longer adequate. Two-factor authentication offers a way to strengthen the security around who has access to organisational systems and data.
What shouldn’t you rely solely on usernames and passwords?
Passwords are vulnerable in a number of ways:
- People write them down if they have trouble remembering them – leaving them open to be stolen.
- People often rely on commonly used passwords – such as “password” or “123456” and are easily guessed.
- People often use personal information such as their pet’s name or place of birth which can be guessed based on information available on their social media accounts.
- Passwords can also be subject to external threats, such as hackers using brute-force attacks and social engineering tactics.
- If you’re using the same password across multiple accounts this leaves you very vulnerable in the event of a breach.
How can I strengthen my access policies and user authentication processes?
The traditional approach of using a password as the sole log-in credential is an example of a single-factor authentication process.
By switching to two-factor authentication you can strengthen the security around the way your users access your organisation’s IT services.
What is two-factor authentication?
Two-factor authentication adds a second step to your traditional single-factor, password-based authentication process.
We already use two-factor authentication in many aspects of our lives. The most obvious example is when we use a chip-and-PIN bank card to make payments. The card is one factor; your PIN is the second.
It is important that the two factors used in a two-factor authentication process are different types of authentication factors.
What different types of authentication factors are there?
The US National Institute of Standards and Technology (NIST) has laid out clear guidelines for multi-factor authentication. It recommends at least two out of three identifiers from:
- Something you know (e.g. a password)
- Something you have (e.g. an ID badge or a cryptographic key)
- Something you are (e.g. a fingerprint or other biometric data)
In our example of the chip-and-PIN payment card, the card is “something you have” and the PIN is “something you know”.
Why do I need two-factor authentication?
Two-factor authentication can strengthen the security around the way users access IT services. By making it harder for hackers to access your systems and network, you are creating a deterrent.
Is two-factor authentication completely secure?
No system is completely secure. Although two-factor authentication is a good improvement over relying on passwords alone, it may not be perfect in all situations.
How does two-factor authentication work?
Most two-factor authentication approaches focus on “something you know” (password) plus “something you own”. More often than not, the something you own is your smartphone or tablet and this is validated by sending an email or SMS message with an access code to your phone or tablet which has to be entered before access is granted.
How does an authenticator app work?
Authenticator apps generate temporary authentication codes, effectively one-time access passwords, based on the particular device, user or account, that must be recognised as valid by the authenticator app.
Why is an authenticator app better than an SMS-based authentication?
Once set up, authentication work even when you don’t have access to your phone network – making them more convenient for users than SMS-based authentication. They are also more secure since they can’t be intercepted in the same way an SMS message can be.
What does Netstar recommend?
Organisations should definitely implement a two-factor authentication process as a minimum wherever possible.
We recommend and install various authentication methods for our clients, based on their needs. We also recommend that all our clients carry out a standardised company-wide implementation, so that everyone has two-factor authentication on their machines, thereby ensuring optimised security.
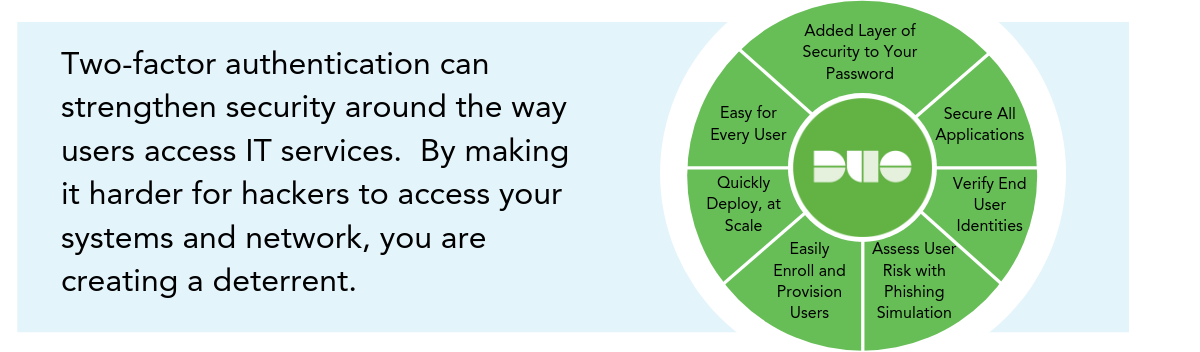
The Duo authentication app makes the authentication process faster and easier. Learn more about how it works below.

What is Duo?
Duo is an app that makes it easy for organisations to implement two-factor authentication. Typically, users simply download the Duo app to their mobile device. When logging in, they enter their username and password as usual, then use the phone app to verify their identity.
You can link multiple devices to each account.
What’s more, Duo gives organisations the flexibility to create and enforce strong access policies according to certificates, device versions and security configurations. It also checks the security health of devices before they access applications and makes this information available to administrators through auditing and reporting tools.
Are there any disadvantages to two-factor authentication?
Two-factor authentication does create an extra step for users when logging into your corporate systems. You, therefore, need to educate users about why this extra step is important.
Different two-factor authentication solutions will have different vulnerabilities. Adopting an easy-to-use solution like Duo can help make this process extremely simple to adopt by users.
How can I find out more?
To learn more about two-factor authentication and how it could help you improve your business security get in touch with us today to start a conversation.